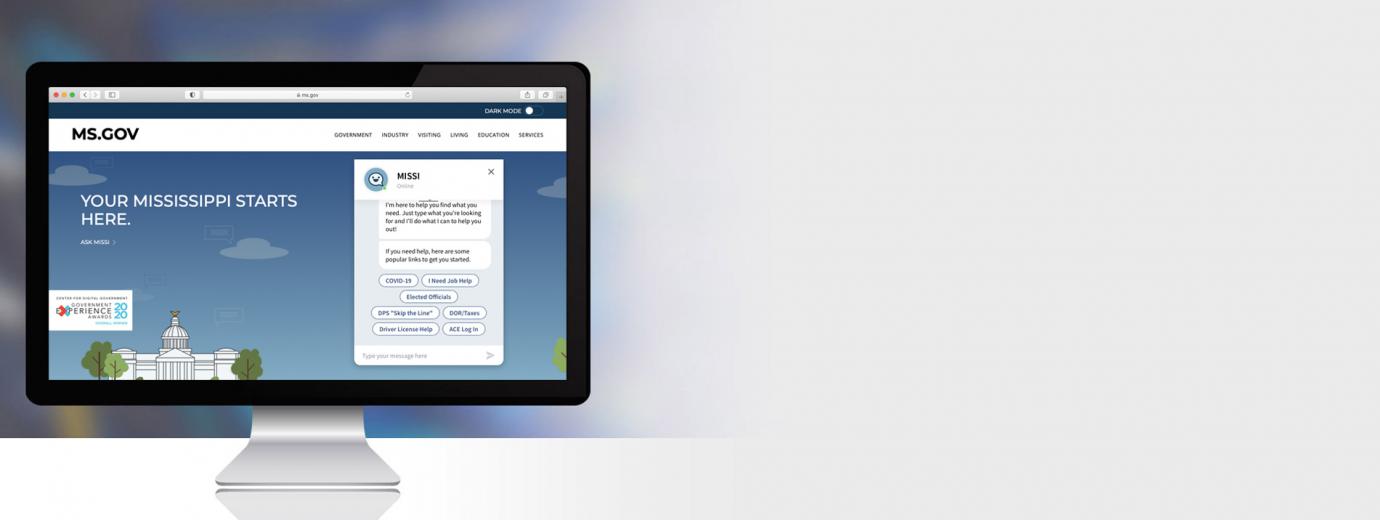
Mississippi Department of Information Technology Services
News & Events
QUICK LINKS
- Board Meetings
- Express Products Lists (EPLs)
- Help Desk and Support
- Enterprise Cybersecurity Incident Reporting
- ITS Staff Contact Information
- Map and Directions
- Procurement Award Information
- Prohibited Technologies List
- RFPs and Sole Sources
- Security Advisories
- State Government Telephone Directory
- Technical Training
- Vendor Information
- Wireless Communications